If it feels like eons have passed since the last major pfSense release, in an IT sense, that is close to being accurate. The last “dot” release of pfSense, the popular firewall appliance platform, occurred with the pfSense 2.4.5 release in March 2020. The previous “4” digit incremented with the pfSense 2.4 release in October 2017. Now, in February 2021, we have pfSense 2.5 which is perhaps the biggest upgrade in years.
pfSense 2.5 Release
We previewed the release a bit in pfSense adding WireGuard VPN and pfSense Plus. With this edition, the project will be more formally segmented into the open-source pfSense and the higher-end pfSense Plus. You can read more about that change in the link above. There are a number of big changes in this version, and some of it comes from the basic underpinnings. While pfSense 2.4.5 was based on FreeBSD 11.3, pfSense 2.5 is based on FreeBSD 12.2. We also get a host of changes to basic components such as an OpenSSL upgrade.
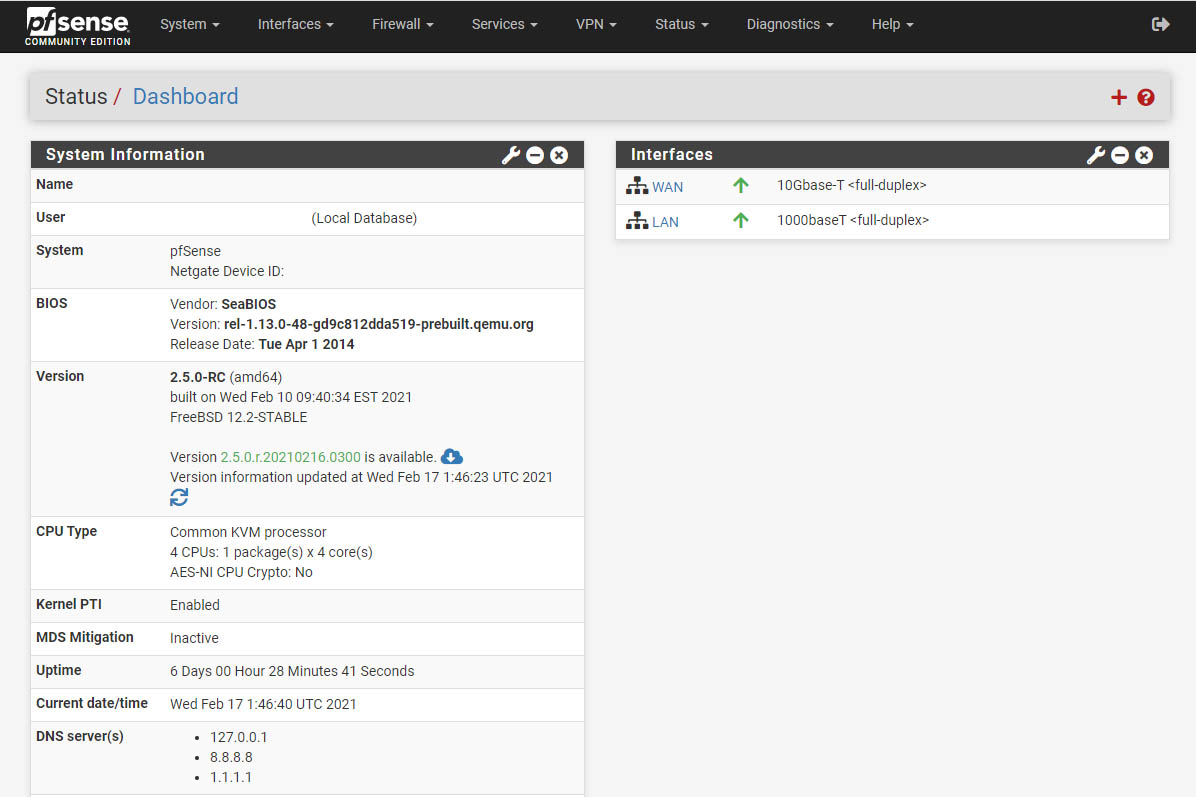
One of the headline features is the ability to add a kernel-based WireGuard tunnel in pfSense. This is available in the UI, however, there is not a lot of contextual information other than the basics of features. The setup is functional, but not as nice as the OpenVPN wizard.
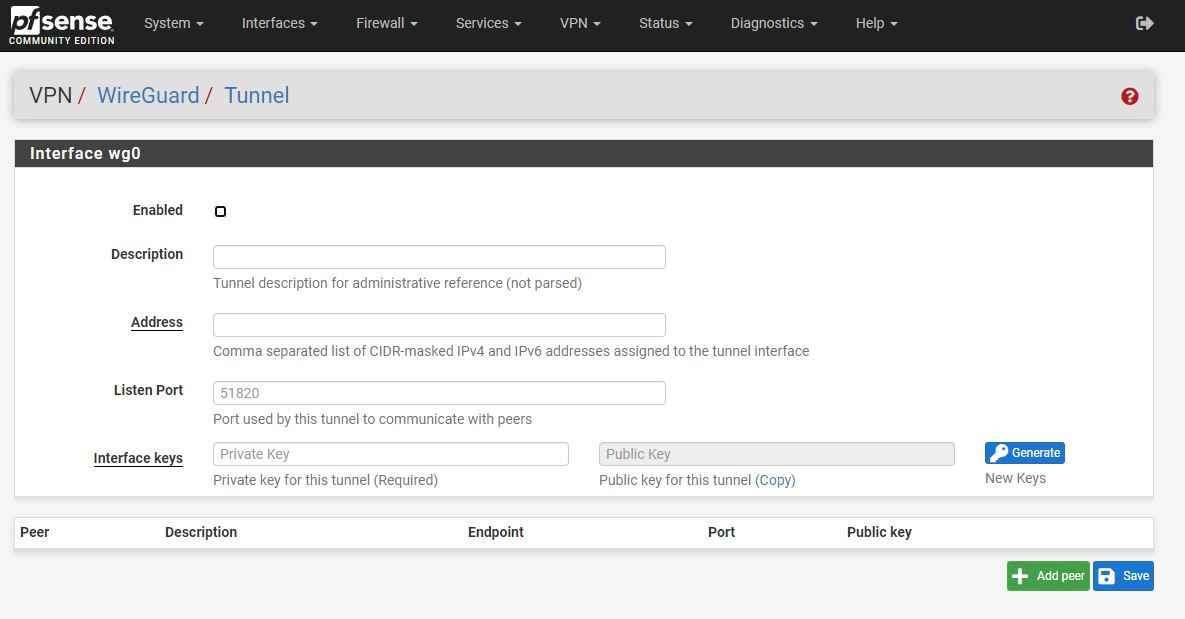
One other interesting feature is that logs in pfSense are changing. Specifically, pfSense is moving to a log rotation solution. There is even a page for controlling those settings. For those of us who enjoy looking at just how many clients are scanning, this is a nice feature. Here is just a look at a recent basic firewall that was setup. You can see just how many entries are created in two minutes using the default firewall rules.
Since this is a release that is 1-3.5 years in the making, there are a lot of changes noted in the Release Notes that you may want to look for. One that we were a bit bummed that did not make it into the RC snapshot we tried is that we checked if pfSense on Proxmox VE has gotten any easier. It still blocked LAN traffic by default with virtio NICs (E1000 works.) We were a bit hopeful with some of the defaults for the checksum offload changing, but this apparently did not make it. It is too bad this does not work out-of-the-box as it is a great way to learn pfSense and not having that out-of-box experience will turn away some users.
Final Words
If you are feeling adventurous, you can always check out the release today. We know some of our users will choose to hold-off waiting for others to upgrade first. Still, If you want to be on FreeBSD 12 with the newer features, then you will want to be on the new version sooner rather than later.
We just hope pfSense 2.5.1 is not around a year away. We understand that pfSense does just about everything one would need for a huge portion of the firewall/router market. At the same time, it feels like development largely stalled just because of the gap between major releases.
As always, a friendly reminder to make a backup before upgrading your existing systems.




Netgate committed to both 2.5 and 2.6 for this year, so I don’t think we’ll be waiting a year for the next release after 2.5.
I’d also recommend that anyone thinking of upgrading to 2.5 read this: https://docs.netgate.com/pfsense/en/latest/install/upgrade-guide-versions.html#upgrading-from-versions-older-than-pfsense-2-5-0
Backup your config.xml file before upgrading. A lot of people also recommend uninstalling all of your packages before upgrading and then installing them again afterwards.
It might also be a good idea to download the install image for 2.4.5-RELEASE-p1 and keeping it handy in case you need to revert to it if 2.5 doesn’t work for you.
I plan to wait a while before upgrading and see what problems, if any, people have so I can try to avoid those problems.
It really feels like it took an eternity, ironically now that its there I’m holding back upgrading … because I have nothing that I really miss and I don’t want to break the stability I have. I’ll probably wait another year or months or maybe just weeks and read about the experiences that others have with it.
* hits the upgrade button and feels like a tool for not doing the backup like suggested at the end *
…normally i skip to the end of your reviews early to find the price :p
i thought I was able to use the proxmox virtio driver OK with pfsense 2.4.5…. I only tested it for a little bit but it seemed to be OK?
And apparently they now changed their license or something, so most new stuff will be part of pfSense Plus – and CE would only get security updates.
2.5.0 is all jacked up. It says installed but system would not reboot at all. Nothing works. I had to reinstall 2.4.5. Sucks.
I used Pfsense for a while but I’m not advanced enough to trust the box.
I went with another solution that is much easier to interact with and whether it is more secure I don’t know but it does feel more intuitive and I can use features in minutes instead of days it took me to activate and test Pfsense features.
If Pfsense made the interface more user friendly I would gladly come back.
Each to their own.
Did they finally do the full rewrite and make it API based on python3 vs. the old static coded python2 stuff?
API calls for automated configuration were a big todo on their list.
No they didn’t. First note in the release notes is they pushed support for the API to a later date due to AES-NI requirements.
It does look like they made the shift to python3 though. I’m interested in how the upgrade works moving from the old python2 versions to the new python3 based one.
This is great news. I just picked up an m90n iot to replace my old celeron build and apparently the stable realtek drivers are included as a package in 2.5
Due to the lack of progress and updates in the past, it felt like Netgate threw pfSense under the bus in favor of TNSR. This is why I have switched to OPNsense.
Most of us saw this coming that the community edition would get screwed over when they announced tnsr. I have zero regrets that I made the switch to OPNsense then and the release of pfsense+ just proved me right even further.
My Problem currently is, that there is no quagga available. So thats the reason, I can’t upgrade yet. But I am waiting for it!
Did the upgrade in place, got frozen on “waiting for device to reboot,” and my whole network was down. Had to run and find my screen and keyboard, attached them to my pfsense box, gave it the 3 finger salute, it restarted, and everything seems to be working fine now, fully updated.
now my qradar ce dsm for pfsense wont show me firewall permits and firewall denies anymore. everything now goes under pfsense message category message.
while wireguard inclusion is good, ntopng returns to default settings whenever the service is restarted or otherwise rebooted.
Otherwise upgrade was success with no issues so far.
The release is very buggy the upgrade on the Apu2 failed, the Uefi installation didn’t work, it stopped booting and I had to switch to the Bios variant. And the best openvpn ignores the set outgoing interface and tries to use the system defaults even when that doesn’t work because it is the vpn tunnel that is supposed to be created. At least a static route to the Vpn server Ip has remedied this for now.
I really don’t have packages on my firewall except for snort. My upgrade did go flawlessly , I haven’t noticed any bugs as of yet , snort still works perfectly, so fingers crossed
I’ve updated an APU2C4 from 2.4.5p1 to 2.5. After adjusting “Fallback Data Encryption Algorithm” to “None (No Encryption)” the setup was working fine with my uploaded backup data from 2.4.5p1. Also Squid and pfBlockerNG Devil are working well. A real impact is the VPN speed even if I’ve used nearly the same settings as my VPN provider taught and were existent under 2.4.5p1. I use OpenVPN with NordVPN and after updating the d/l speed is the half. Under 2.4.5p1 I’ve had about 96mbit now at about 50mbit. I’ve tried different options also under “Allow Compression” in the VPN Client settings but no change achieved so far. If this will ne getting better I’ll go back to 2.4.5p1. Kind regards
For me, the upgrade process itself was pretty smooth, no issues. pfense booted in the new version without problems and pretty fast. But, I immediately noticed that DNS resolver (ubound) did not start up. I’ve restarted it and things got back to normal, but since the upgrade, about 3 hours ago, ubound has already crashed without restarting automatically 3 times or so. This never happened before the upgrade. I’ve read in a few posts that other users using PfblockerNG-Devel had similar problems, but I don’t have pfblockerNG installed. Has anyone else come across this issue?
I’m a bit on the fence about this update. I had my sg3100 freeze up a little over a day after moving to 21.04 where it went into a non-forwarding state and DHCP also died. While a power cycle brought it back to functioning but still concerning. I wasn’t able to find anything in the logs and the watchdog didn’t kick in and reboot it- very interesting.